Bring It On: Cybersecurity Executives Say Their Organizations Are Well Prepared to Meet a Russian Cyber Challenge
Many Western governments are warning of the potential for increased Russian cyberattacks on businesses and national infrastructure as a response to sanctions over the invasion of Ukraine. Nonetheless, more than two-thirds of the 37 risk, strategy, and crisis management executives The Conference Board surveyed between March 10 and March 17 say their organizations are prepared to handle the threat.
Ninety percent of respondents to the poll of members of six US and EU Councils of The Conference Board say the threat of cyberattacks on their organization has increased since the Russian invasion of Ukraine, with 22 percent describing the increase as significant. However, at this point there is no clear evidence the recent rise is related to state-sponsored hacking or a purposeful escalation of cyber warfare. At least not yet.
Judging from our poll, warnings of a looming Digital 9/11 or a Cyber Pearl Harbor—apocalyptic and hopelessly complex threats for which both countries and companies are, if not defenseless, at least woefully underprepared—presents a one-sided picture. Cyber risk is one of many operational risks companies face. From a business viewpoint, mitigation of cyber risk is about fundamental risk management, corporate resilience, and managing human behavior.
Insights for What’s Ahead
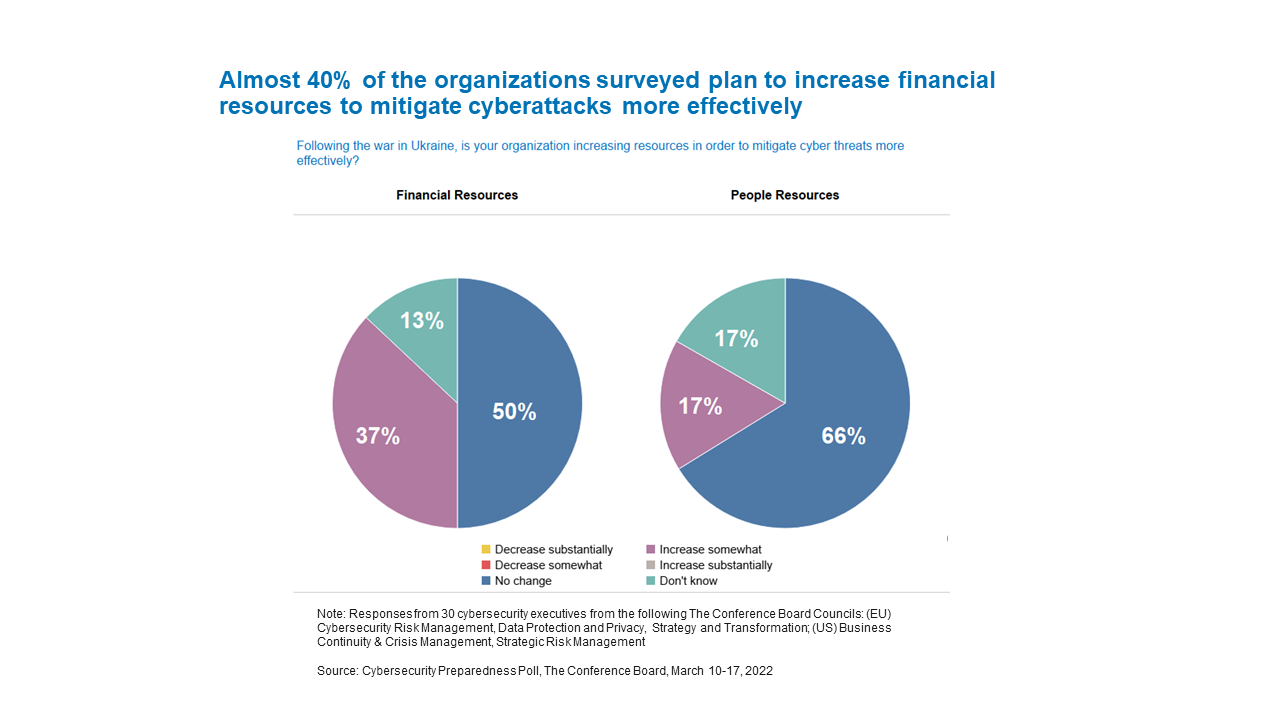
In anticipation of more sophisticated and orchestrated attacks, some organizations are putting more resources toward their cyber risk defenses. Even though our responding executives express confidence in their organizations’ ability to deal with an increased threat, they are not being complacent. More than a third (37 percent) say their firms have increased financial resources dedicated to cyber risk since the Russian invasion of Ukraine, and 17 percent have added personnel to deal with the higher threat levels.
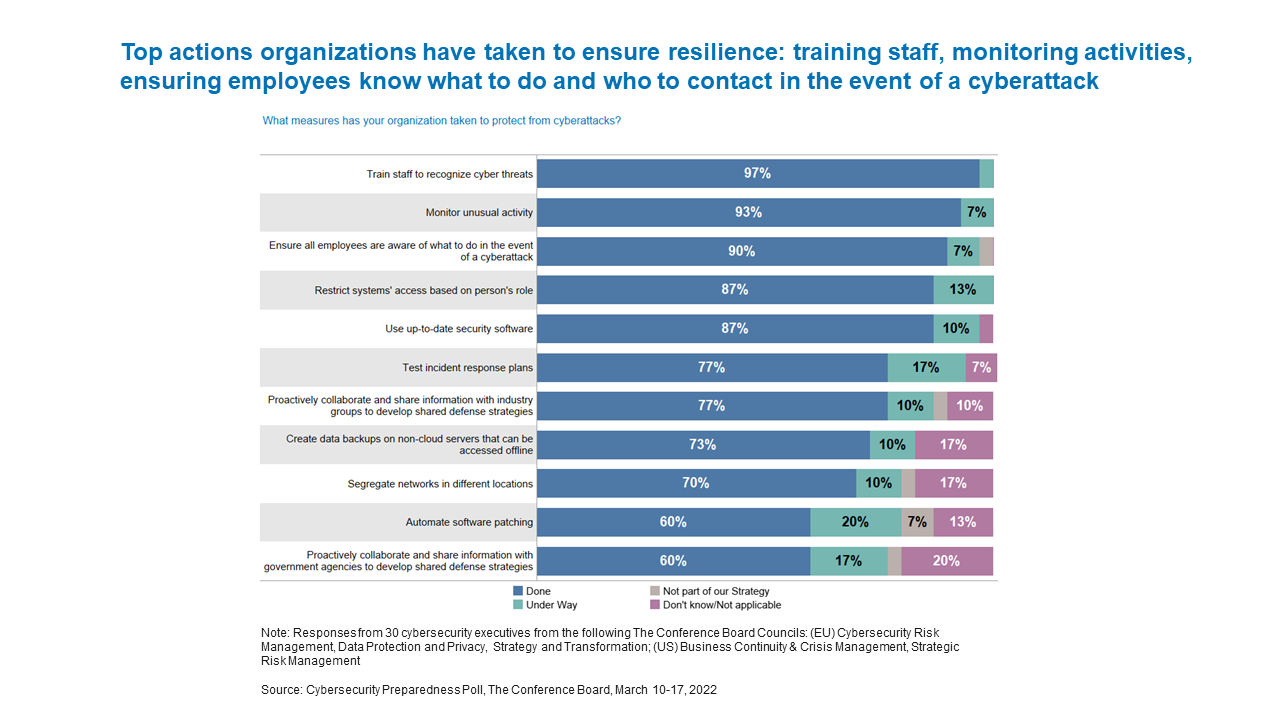
It’s not just a technology issue: humans are the weakest link in the cybersecurity chain, which is why organizations are emphasizing employee training. Increases in remote working and remote access to networks and corporate data have made many organizations more vulnerable. Train staff to recognize cyber threats is the most frequently cited mitigation strategy firms are deploying (97 percent) as threat levels elevate. Monitor unusual activity is second at 93 percent, and ensure all employees are aware of what to do in the event of a cyberattack is third at 90 percent.
Protection of national security and infrastructure needs to be a shared responsibility with private sector companies, especially in the US. According to the Federal Emergency Management Agency (FEMA), the private sector owns the vast majority of the US’ critical infrastructure and key resources—roughly 85 percent. While 77 percent of responding executives say their organizations proactively collaborate and share information with industry groups to develop shared defense strategies, just 60 percent say they share such information with government agencies for that purpose. When managed effectively, the benefits of sharing threat information, including sensitive business information, mitigate the risks. Quicker access to the kind of cyber intelligence governments collect can help companies develop more effective and innovative responses. Establishing liaisons up front, understanding protocols, and laying out the sharing framework in advance is critical to effective overall risk management and mitigation.
Taking Preventative Action Post-Invasion
Conversations with Members of The Conference Board Cybersecurity Risk Management Council in Europe surfaced the top five actions companies are taking now to enhance security following the Russian invasion of Ukraine. They are:
- Segregating global networks and limiting access from Ukraine and Russia to protect the overall system. This isn’t a black-and-white issue: companies continue to provide humanitarian assistance in these areas while working to avoid violating sanctions.
- Increasing focus on threat intelligence. While threat intelligence is a daily part of information security’s role, in this environment, companies adhere to the saying, "Never waste a good crisis.”
- Applying higher rigor in the assessment of normal IT operations. Security experts are ensuring IT tools have the latest updates; everyone is paying extra attention to insider threats.?Companies are relying on technology partners and will engage external specialists as needed.
- Paying attention to the impact of corporate statements and any unintended consequences.Vilifying the invasion in a strongly worded statement could make that company a target for hackers. Companies want to support their employees from Ukraine and from Russia without making them the enemy.
- Developing a playbook for employees to follow in case of a major attack. Organizations are shoring up C-suite support while also empowering local decision-making.
Building a Cybersecurity-Conscious Internal Culture for the Long Term
Because today’s advanced cyberattacks focus more on exploiting human flaws than system flaws, a cyber risk management strategy that depends exclusively on technology as its primary defense will be inadequate. (See: C-Suite Challenge™ 2020: Data Privacy and Cybersecurity—Mitigating Risk, Seizing Opportunity.) Building a security-conscious culture requires business leaders to:
- Raise awareness. Explain and give examples of common behavior that puts the organization at risk.
- Instill ownership by making employees accountable. Push responsibility down to the business units and the individual. Organizations that have instituted a bring-your-own-devices program need to help individuals understand their personal responsibility and that they will be held accountable for failing to follow standards and procedures.
- Change the narrative. Emphasize that cyber and information security practices are an essential business enabler and not an inconvenient impediment to be overcome. Describe specific repercussions of various cyber breach scenarios to make potential risks more relatable. Companies with impactful cybersecurity training understand that training and awareness is a continuous process, not just an annual check-the- box exercise. Effective awareness campaigns personalize the message: “Here is what a phishing attack could do to compromise your personal identity or finances, so practice this kind of technology hygiene at work and at home.”
- Educate managers and employees to identify information security risks and act accordingly. They also need to be reminded that they should be modeling compliant behavior for the rest of the organization.
- Monitor employee awareness levels. Cyber and data security preparedness is not a static state. Without consistent and constant communication, the level of security awareness will ebb and flow.
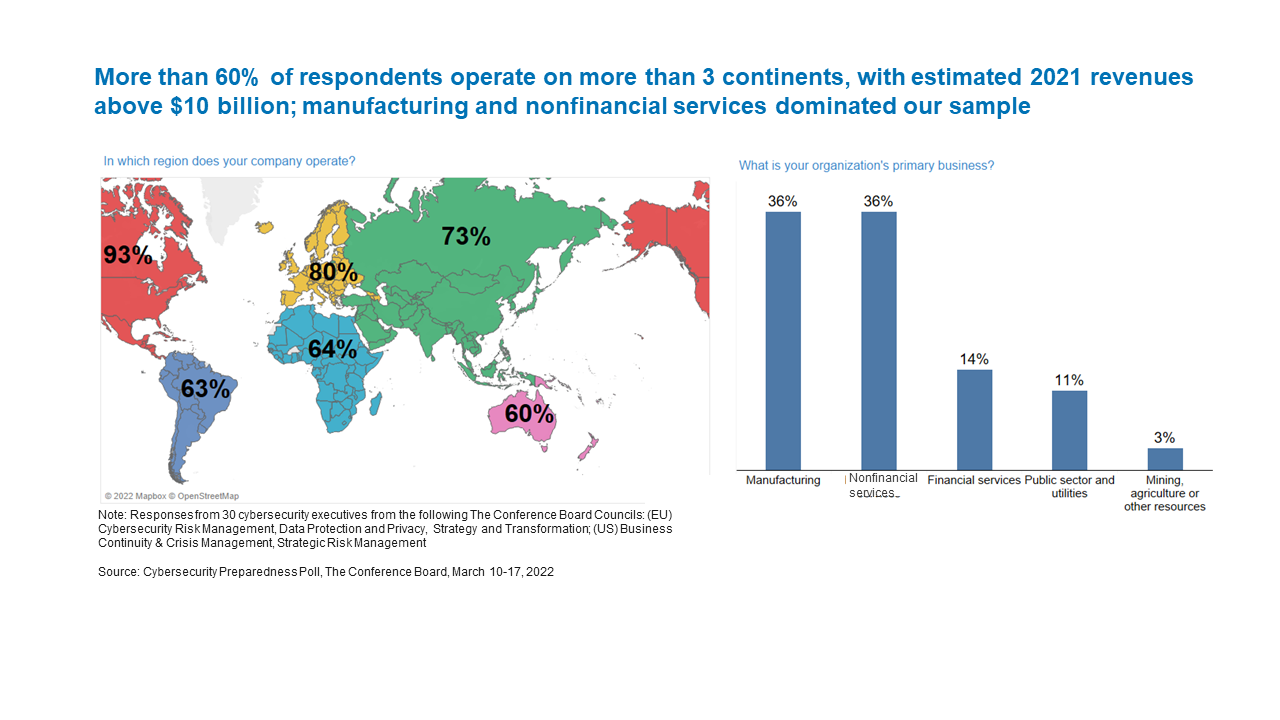
Demographics